Secure Your Data Anywhere With Universal Cloud Storage
In an era where data safety and security is extremely important, companies and people seek dependable remedies to safeguard their info. Universal Cloud Storage space offers a compelling choice for those looking to firmly save and gain access to information from any area. With its advanced file encryption protocols and functional availability functions, this solution makes certain that data remains available and protected whenever needed.
Advantages of Universal Cloud Storage
Universal Cloud Storage space uses a myriad of advantages, making it an important device for safeguarding and accessing data from various areas. Customers can access their information from anywhere with an internet link, allowing seamless cooperation among team members no matter of their physical place.

Information Security and Safety And Security Measures
With the increasing dependence on cloud storage space for data accessibility and partnership, making sure durable data encryption and security measures is necessary in securing sensitive information. Information encryption plays an important function in securing data both in transportation and at rest. By encrypting data, information is exchanged a code that can just be analyzed with the suitable decryption secret, including an added layer of security against unauthorized access.
Carrying out strong authentication approaches, such as multi-factor verification, helps confirm the identification of individuals and protect against unauthorized individuals from acquiring accessibility to sensitive data. Routinely updating safety procedures and spots is necessary to ensure and resolve potential vulnerabilities that safety measures continue to be effective versus evolving threats.
Furthermore, using end-to-end encryption can provide an extra level of protection by making certain that information is encrypted from the factor of origin to its final destination. By embracing a detailed strategy to information security and security measures, organizations can improve information protection and mitigate the risk of data breaches or unapproved access.
Access and Cross-Platform Compatibility
Making sure data ease of access and cross-platform compatibility are crucial considerations in optimizing cloud storage remedies for seamless user experience and effective partnership. Cloud storage solutions need to provide users with the ability to access their information from different devices and running systems, guaranteeing efficiency no matter of area or technology preference.
By providing cross-platform compatibility, individuals can seamlessly change in between tools such as desktops, laptop computers, tablet computers, and smart devices without any kind of obstacles. This flexibility improves individual convenience and productivity by permitting them to service their data from any device they choose, promoting partnership and efficiency.
Moreover, accessibility functions such as offline access and synchronization guarantee that users can watch and modify their information even without a web link. This ability is crucial for individuals that frequently work or take a trip in areas with poor connection, guaranteeing uninterrupted access to their crucial files.
Backup and Catastrophe Recuperation Solutions
To strengthen data honesty and functional connection, durable back-up and calamity healing options are essential parts of an extensive cloud storage structure. Back-up options make sure that data is regularly replicated and kept securely, reducing the risk of information loss because of unintentional removal, corruption, or cyber threats. Calamity recuperation options, on the other hand, focus on quickly bring back procedures in the occasion of a devastating event like all-natural calamities, system failures, or cyber-attacks.
Efficient back-up techniques involve producing numerous duplicates of information, keeping them both locally click to find out more and in the cloud, and carrying out computerized backup processes to make certain uniformity and integrity. Universal Cloud Storage Press Release. Catastrophe healing plans consist of predefined treatments for data repair, system recovery, and functional continuity to lessen hop over to these guys downtime and alleviate the effect of unforeseen disruptions
Finest Practices for Data Protection
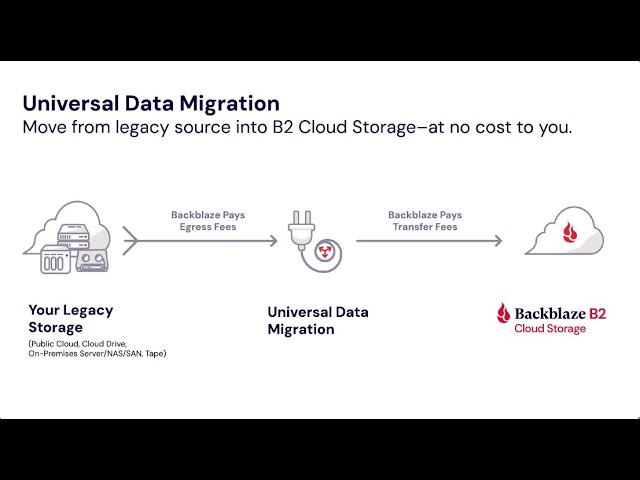
Furthermore, developing and imposing data backup procedures makes sure that information can be recuperated in the occasion of a cyber incident or information loss. By sticking to these finest methods, organizations can enhance their information defense strategies and minimize potential dangers to their information properties.
Conclusion
Finally, Universal Cloud Storage space supplies a protected and dependable option for storing and accessing data from anywhere with a web useful reference connection. With durable file encryption measures in position, information is protected both en route and at remainder, guaranteeing privacy and honesty. The availability and cross-platform compatibility attributes enable smooth cooperation and performance throughout different devices and running systems, while back-up and disaster recuperation solutions supply comfort by guarding against data loss and ensuring quick reconstruction in case of emergency situations.
